Authentication Requirements
Use Cases
- SUBSET OF MIT COMMUNITY: Standard for most MIT Administrative Applications
- UNSECURE PORT: If user tries to enter the application via a non-SSL (unsecure) port then the application should display a page that does the following:
- Display a statement saying that this application requires a client certificate
- Displays a link to tell the user how to obtain an MIT issued certificate.
- Gives the user the SSL version of url for them click
- NO CERTIFICATE: If the user tries to enter the application via the SSL (secure) port and the user does NOT have a valid MIT issued client side certificate then the user should be routed to the non-SSL port in (1) above telling them how to get an MIT certificate.
- ACCESS DENIED: If the user has a valid client certificate but does not have ANY authorizations for this particular application then the application should display a page that tells user who to contact to get the required authorization.
- VALID USER: If the user has a valid client certificate AND at least one authorization for this particular application then the user should be allowed into the application.
- IMPERSONATE: If the user knows the right password she can log in as another user, get the roles of that other user and look to the system as the other user.
- UNSECURE PORT: If user tries to enter the application via a non-SSL (unsecure) port then the application should display a page that does the following:
Authentication List
- Cannot just get a String, need to be able interrogate type of token.
- User user = securityMgr.getCurrentUser ();
- user.getType (); (i.e. Kerberos, MIT ID, email address, Alumni ID, etc)
- user.convertTo (type); - allows programmer to convert between supported types
- Service layer access to authenticated user without having it explicitly passed in each call
- i.e. User user = securityMgr.getCurrentUser (); works on service layer just as it does on the web tier
- A way to do machine to machine authentication (or app to app authentication)
- An ability to invoke service method on behalf of a named business user
- Ability to impersonate another for testing just within a particular application
- Grant Impersonate to X for application Y
- UI to let X type in user Z to impersonate them within the rest of the application
- User user = securityMgr.getCurrentUser (); // must return Z
- User user = securityMgr.getTrueUser (); // optional to return X
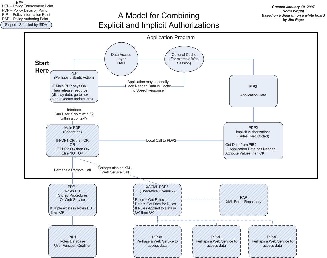
Authorization requirements
Below are the documents that came out of the GASP/ISDA meetings:
AuthorizationModelForCombiningExplicitAndImplicitAuthorizations.vsd