...
Here is an example of the Shibboleth handler settings section (in the General settings tab) for the authentication module when used at MIT, for the host name ist-dev.mit.edu. Click on the image to enlarge it.
...
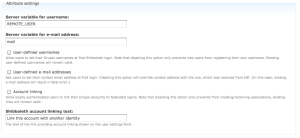
A typical attribute settings section (in the General settings Tab) is shown below. Click on the image to enlarge it.
The entries in the Shibboleth handler settings screen shot above assume that you have used the MIT gen-shib2.sh shell script to configure your shibbolethshibboleth2.xml file. You should check your shibboleth2.xml file. Within the "Applications" section, look for the SessionInitiator section. You should have one SessionInitiator that is defined as. If you are running Shibboleth SP 2.4 (or higher), you may have a single SSO element within the Sessions element; this configures the login handler location at /Shibboleth.sso/Login:
| Code Block |
|---|
<SSO discoveryProtocol="SAMLDS" discoveryURL="https://wayf.mit.edu/DS">
SAML2 SAML1
</SSO>
|
Pre-2.4 configurations will have a section of SessionInitiator elements within the Sessions element; the first one (default) should look like:
| Code Block |
|---|
<SessionInitiator idtype="ISDAChaining" Location="/Touchstone" Binding="urn:mace:shibboleth:sp:1.3:SessionInit wayfURLDS" isDefault="true" id="MIT-DS" relayState="cookie"> <SessionInitiator type="SAML2" acsIndex="1" template="bindingTemplate.html"/> <SessionInitiator type="Shib1" acsIndex="5"/> <SessionInitiator type="SAMLDS" URL="https://idpwayf.mit.edu/WAYF/WAYF" wayfBinding="urn:mace:shibboleth:1.0:profiles:AuthnRequest" /> DS"/> </SessionInitiator> |
Note that the Location setting here is /DS, so you would use /Shibboleth.sso/DS as the URL of the login handler.
The elements The SessionInitiator shown above will direct users to the MIT WAYF/DS (Where Are You From/Discovery) server. This is appropriate if you have an application that will support users from outside of MIT as well as users that have an MIT Kerberos username.
If your application is intended to only be accessible to users that have an MIT Kerberos username then you should have a SessionInitiator as followsspecify the MIT IdP entityID (https://idp.mit.edu/shibboleth) as a property of the SSO/SessionInitiator. For a ![]()
SessionInitiator, an example of this, using the /Login location, is:
| Code Block |
|---|
<SessionInitiator idtype="MITChaining" Location="/MIT-only" Binding="urn:mace:shibboleth:sp:1.3:SessionInit" wayfURLLogin" id="MIT" relayState="cookie" entityID="https://idp.mit.edu/shibboleth-idp/SSO" wayfBinding="urn:mace:shibboleth:1.0:profiles:AuthnRequest" /> |
...
">
<SessionInitiator type="SAML2" acsIndex="1" template="bindingTemplate.html"/>
<SessionInitiator type="Shib1" acsIndex="5"/>
</SessionInitiator>
|
Group rules allow you to automatically map Touchstone-authenticated users to specific Drupal roles, based on values in SAML attributes. One common attribute we use here is "affiliation". Here is an example of configuring the Group Rules when using Drupal 6. Click on the image to enlarge it.
...